Introduction
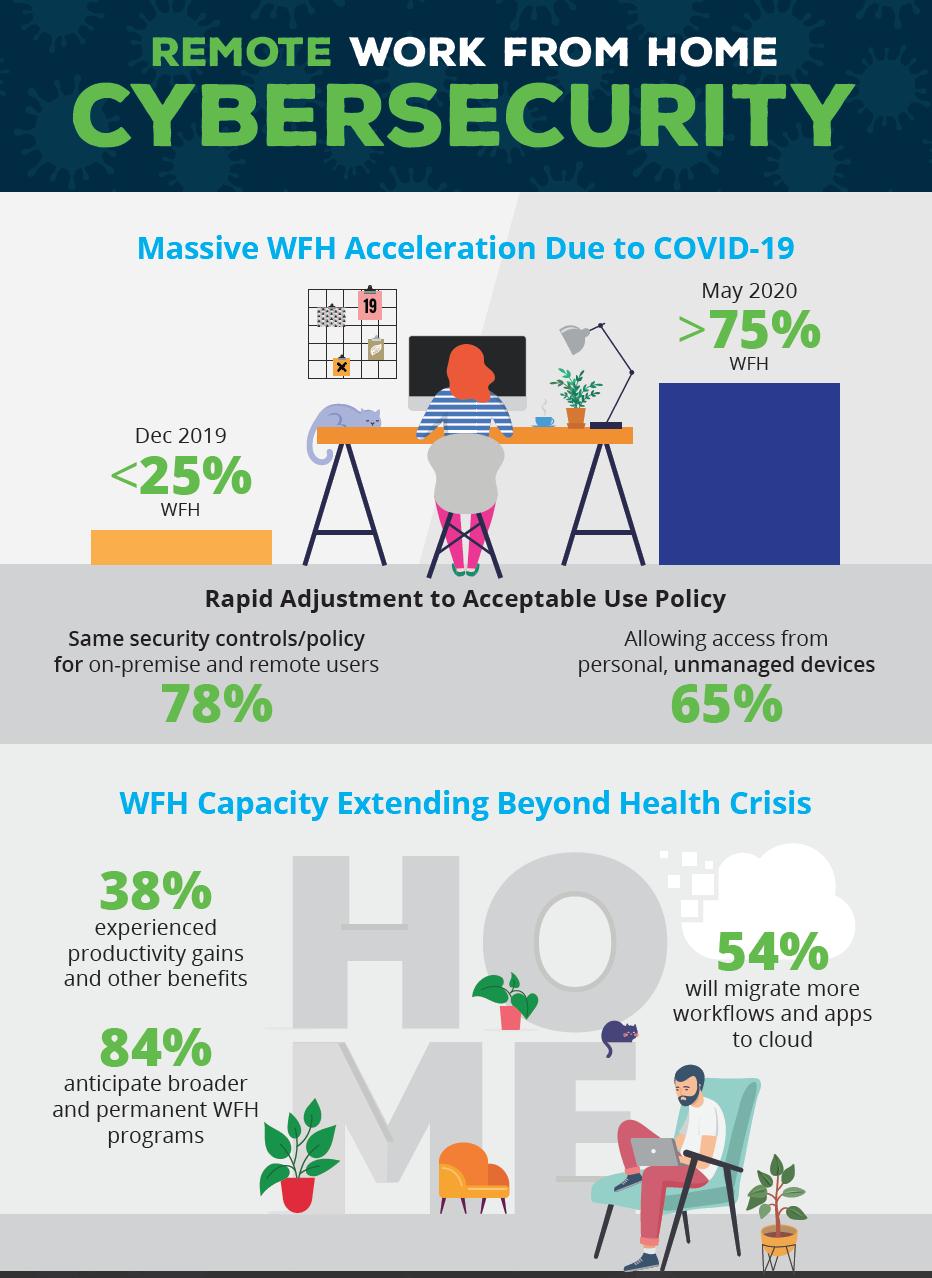
If you own a business or work as a freelancer, you know that the term "work from home" implies a wide range of remote working arrangements. For instance, some employees work remotely for one day per week, while others do so occasionally when traveling for training purposes and so on.
While this flexibility is great for businesses, it also creates several new challenges regarding data security and compliance.
Here are our top nine that will help you stay secure while allowing your employees the freedom to work remotely!
But first, let's cover what remote work security is and why it's essential for your business.
What Is Remote Work Security, And Why Is It Important?

Remote work is a growing trend, and it's not just because the Internet is making everyone attached to their homes or residences.
Remote working teams are more productive than their office-bound teammates. They're also more flexible, allowing companies to scale up or down as needed without hiring or firing anyone.
Besides this, remote work can also optimize company expenditure. That is because renting physical office spaces cost thousands per month. This figure covers the rent, excluding other expenses such as maintenance costs, etc.
Great! Now let's get into the best practices you can start implementing in your business for remote security.
Remote Security Best Practices for Business
1. Designing Data Security Policy
A data security policy is a set of rules and procedures that protects sensitive data from unauthorized access, use, disclosure, modification, or destruction.
Such policies must focus on the following aspects:
- What information do you collect? How do you collect it?
What do you do with it after collection?
- Who can access your information? How are they authorized
to do so?
- Who has control over what parts of your systems?
When looking at your organization's security, it's essential to consider all the different ways sensitive data can be accessed and used.
A good data security policy will cover both internal and external threats.
- Internal threats are the ones you need to worry about when your employees use their own devices or share information outside work hours.
- External threats come from people who aren't part of your organization but want access to its data for malicious purposes- like identity thieves or competitors trying to steal trade secrets.
2. Following Compliance and Security
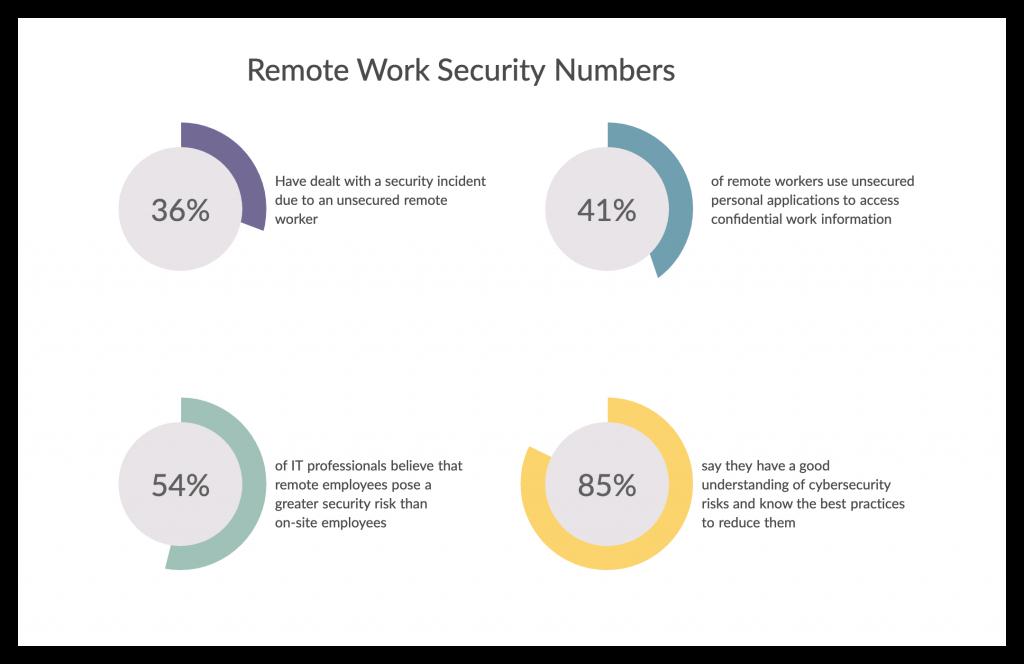
With so many employees working remotely, ensuring compliance with industry regulations and other legal requirements is difficult.
In addition, businesses need to ensure that their data is secure while employees work from home or on the road.
These concerns can be addressed by leveraging log monitoring technology. This form of security software allows companies to monitor employee activity and detect potential threats in real-time.
The data collected from this software can also be used to help companies comply with various laws and regulations, including GDPR, HIPAA, SOX, DSS, PCI, and many more.
3. Migrating Business Applications to the Cloud

Migrating business applications to the cloud is a good way to ensure security and reliability. The following are some of the benefits of migrating your business applications to the cloud:
- Security. Cloud-based applications tend to be more secure than those hosted on-premises because they're not reliant on a single server or network. For example, hackers can access all systems using that server through one breach point if there's an intrusion into an on-premises system. In contrast, data stored in a remote location is harder for hackers to access unless they break into multiple servers simultaneously (which is significantly less likely).
- Reliability. Cloud-based apps are more reliable than their on-premises counterparts because they're monitored 24/7 by IT professionals, who have access rights necessary for addressing any issues that arise quickly and efficiently, such as corrupted databases or failed hardware components.
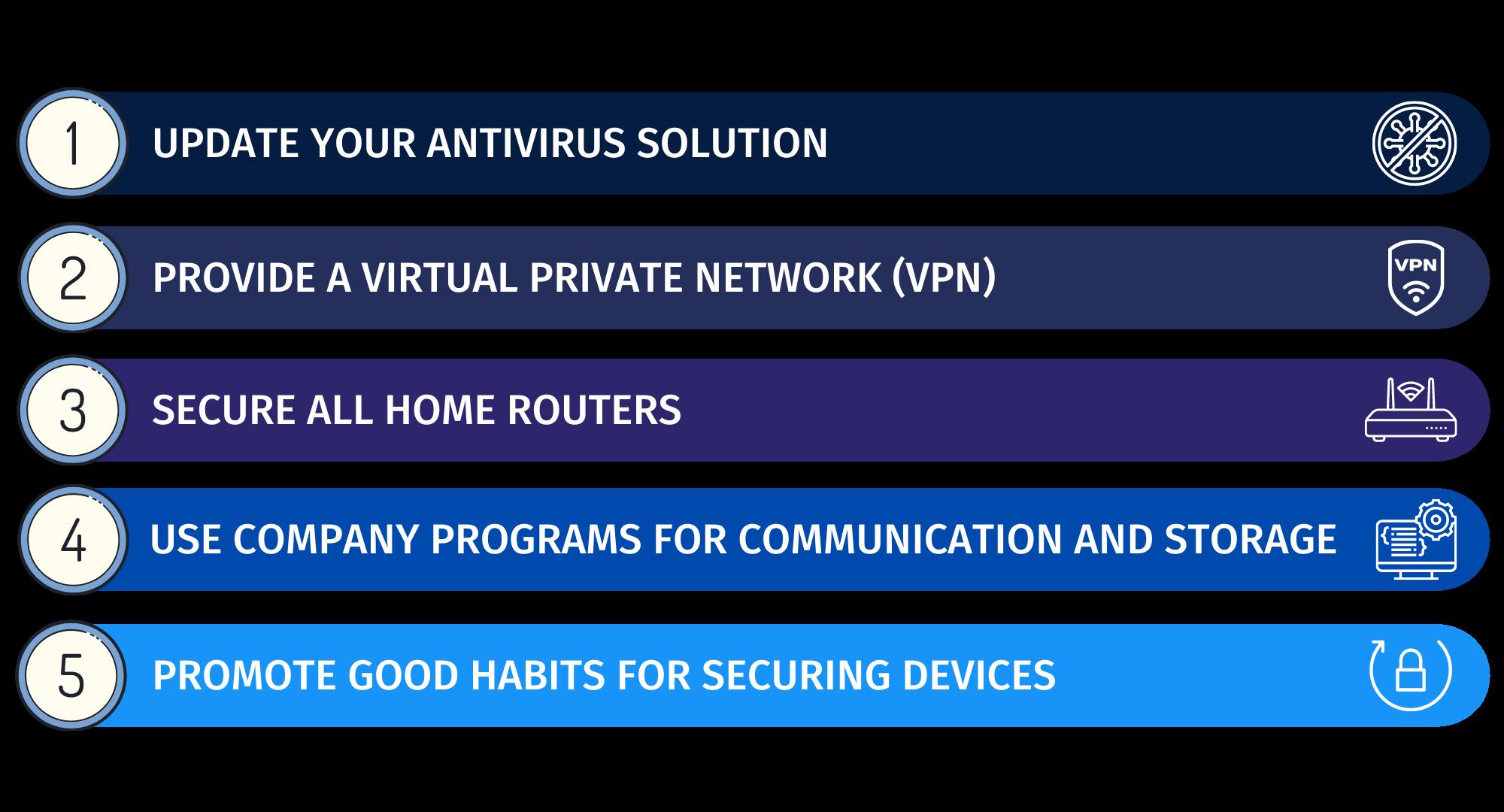
4. Encourage Employees to Connect Over VPNs

VPNs, or Virtual Private Networks, are one of the best ways to protect your data from malicious attacks (like malware and phishing attacks).
They're also a great way to prevent data leakage by encrypting online traffic and making it difficult for hackers to get their hands on sensitive information if they do manage to break into your network.
VPNs are also useful for protecting your data when using public Wi-Fi hotspots. This is particularly important if you're using a laptop since it's much easier for hackers to snatch your data from an unsecured network than it is from a desktop computer.
If you want to ensure that your data remains private when you're on the go, ensure that your employees are all connected via VPN before logging onto any public networks.
5. Installing Multi-Factor Authentication
A multi-factor authentication, or MFA, is a way to make your business more secure by requiring multiple pieces of information to verify your identity.
This can include asking for something only you know (like a password), something only you have (like your phone), or a combination of both.
MFA is beneficial because it adds an extra layer of protection against unauthorized access and even malicious attacks! It's especially useful at work since many employers provide access to sensitive company data through their networks and systems.
Here's how MFA works: If an employee tries to log in without entering their password plus an additional piece of information from one of those options mentioned above, they'll be asked for two different things before gaining access.
For example, their phone number, If the correct answer isn't entered within 30 seconds after being prompted again - or if any incorrect answers are entered - then they won't be allowed into their account until they call HR/IT support.
6. Using Password Managers
Using a password manager can be a great way to manage your passwords and keep your accounts safe.
They generate strong passwords and store them in an encrypted vault that's accessible from any device.
These are the best practices for using these tools:
- Use two-factor authentication wherever possible.
- Avoid using the same password for multiple accounts; this is important if you use a password manager that syncs across devices.
- Be careful when sharing credentials with others, whether
it be through email or text - this allows hackers to gain access to your
account by compromising those who have access to such information.
7. Investing In Antivirus Software
Antivirus software is a must-have for any business that offers WFH.
If you don't have it, then your employees are putting your data at risk. You may not realize how much value lies in those files, but without antivirus protection, hackers can steal and sell them to the highest bidder on the dark web.
Additionally, if someone brings a virus into your network from home or another source (like an unsecured Wi-Fi), it can instantly infect your computer and cripple your entire company for days as IT tries to fix things up again.
This is why you must:
- Choose well-known providers with good reviews.
- Install and update regularly Like any other piece of software you use daily - from word processors like Microsoft Word to browsers like Google Chrome.
- Antivirus programs need regular updates for their features
to work properly and stay up-to-date with new threats that could harm your
system.
8. Data Encryption

Encryption is a great technique to protect your company's intellectual property and sensitive information from prying eyes. Both encryptions at rest and in motion can be used to protect data.
Encryption at rest refers to the process of encrypting files or databases before they're stored on a disk or tape. As for encryption in motion (or en route), this refers to transmitting encrypted messages between two parties (e.g., between employees using email).
Encrypting sensitive data helps ensure its safety both on-site and while it's being transmitted over networks - so there's no need for worry if you want your employees working remotely with sensitive corporate information while they're away from their desks!
9. Phishing Awareness Program/Webinar
In this section, you'll learn about WFH security tips regarding phishing and the best ways to protect yourself. Let's start with what phishing is.
Phishing is when a malicious individual sends a fraudulent email that appears to be from someone in your company or an entity you trust - a bank, for example.
The intention behind their actions is to trick you into giving them access to sensitive information such as passwords or credit card numbers, or trick you into clicking on a link that downloads malware onto your computer.
How do you spot a phishing email? The most obvious sign is an out-of-the-norm email address like "info69@companyname.com" instead of "helpdesk33@companyname.com".
Other signs include misspellings or suspicious grammar, excessive capitalization, long chains of emails (which may be part of an attempt at social engineering), and attachments containing files with names like "invoice_invoice_.exe."
Also, check to ensure that the email is coming from an address within your organization.
Conclusion
In conclusion, we can say that these privacy tips for businesses steps are simple and easy to follow for small businesses, but if you want to enhance your remote work security, then there are advanced ways to do so.
For example, companies can hire an IT expert who will help them with all these things mentioned above or invest in some other software that will automate some processes.


